IP address restrictions
IP address restrictions is a feature to restrict users of the services using source IP addresses.
For example, you can allow the use of Kintone only to the IP addresses of your company to prohibit unauthorized access from third parties.
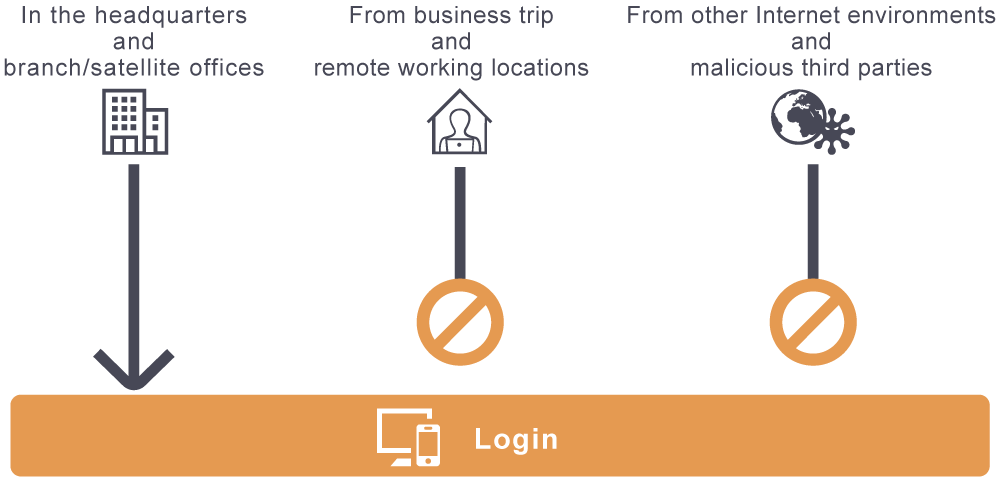
If you want to allow access from remote locations during business trips or the remote workplace outside the office, consider enabling the two-factor authentication.
If IP address restrictions does not meet your need
If IP address restrictions does not meet your need
In the following cases, it is hard to block unauthorized access from third parties with IP address restrictions.
- When you use Kintone on your smartphone, or your source IP address changes dynamically (due to remote work, for example).
- When you access from the IP address shared by many other anonymous users (shared office or public wireless LAN, for example).
Consider using the two-factor authentication.
For details, refer to the following page:
Two-factor authentication
